The new browser by Google called Google Chrome is now available for download in various languages on the Google Chrome website. The installation file has a size of 474 Kilobytes on Windows XP and downloads additional components during installation. The first thing that users will realize after starting Google Chrome is that it will import bookmarks from Firefox and Internet Explorer blazingly fast. It took no longer than a second to import all of my Firefox bookmarks into Google Chrome including the saved passwords, browsing history and search engines.
If you remember the comic that introduced Google Chrome or the article on Ghacks or at other websites you might remember that Google Chrome uses tabs that are independent from each other. If you analyze the computer memory usage of the browser you need to check all instances of chrome.exe that are visible in the Windows Task Manager which is one instance of chrome.exe for the browser itself and another instance for every open tab that displays a website on the Internet. The interesting fact about this method is that the browser will never use more memory than it needs and that the memory will be cleared completely when the user closes a tab. This principle works extremely well during the tests.
Websites are loading faster than in other browsers which can be attributed to the new Javascript rendering engine and the browser engine. Everything about Google Chrome feels faster than in the other browsers.
Speed is one of the major factors of each browser but what about other features and compatibility? Google Chrome is displaying all websites that I tested perfectly fine. I went to flash video game websites, blogs, websites from corporations and some social news websites and everything seemed to display correctly.
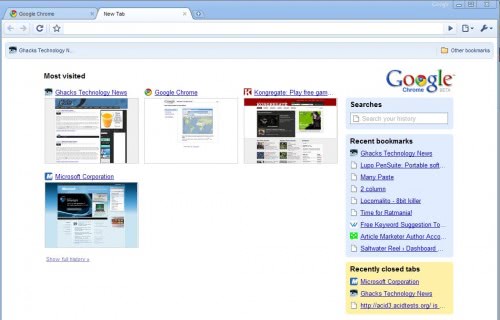
The new tab feature which displays the most visited websites plus the last closed websites plus the last websites that have been added to the favorites and a search function works extremely well and is time saving most of the time.
The Google Chrome Task Manager was another feature that sounded pretty exciting. It displays a Task Manager that is displaying the memory usage, cpu and network stats for the browser, all open tabs and plugins. This makes it easy to identify a process that is using lots of memory and end it right away in the interface. It also contains a Stats For Nerds link which opens the about:memory configuration in the browser which displays detailed statistics about the memory usage.
Google Chrome basically uses the same keyboard shortcuts that all browser share. CTRL T opens a new tab, CTRL N a new windows and so on. The Task Manager can be opened with SHIFT Escape. There is a handy shortcut to perform a search on the default search engine. Pressing CTRL E puts a "?" in the address bar and a search will be loaded for the phrase that the user enters afterwards. This is focusing the address bar automatically. CTRL Shift N opens a window in incognito mode, the mode where no data is saved on the computer.
The Google Chrome beta version is impressive. It lacks a few features that are very important to users like an adblocker or the option to disable scripts but it's pretty good for a beta version. The part of the url that starts behind the domain extension is not that readable, some options to change those colors would be welcome.
The browser is showing lots of promise already. It would be nice if Google Chrome would offer more options to customize the interface and settings.
Google Chrome Now Available